- Kindly bear with us when you find things changing. We are working to make the site better! Wrapping up in a few days.
Global Cybersecurity Threats Analysis: Trends, Targets, and Tactical Defenses (2024 Report)
- 4 May 2025
- Posted by: Benedict Kiprono
- Category: Articles Data Storytelling

Introduction
What are the biggest threats in cybersecurity today, and who’s most at risk? With increasing digitalization, understanding global cyberattack patterns has never been more crucial. This comprehensive analysis dives into real-world cybersecurity incidents from around the world to uncover the most common attack types, vulnerable industries, leading threat actors, and the most impactful vulnerabilities. Whether you’re an IT professional, policy maker, or security-conscious organization, this data-driven report provides essential insights to help you anticipate, defend, and recover from cyber threats in 2024 and beyond.
- Objectives
- Finding the most common attack type.
- Finding the most targeted industry.
- Identifying the attack types that results to the most financial losses.
- Identifying the attack types that affect a highest number of users.
- Identifying the most attacked country.
- Identifying the most common vulnerability type.
- Identifying the most commonly used defence system.
- Identifying the leading countries per attack type .
- Identifying the leading industries per attack type.
- Finding if security vulnerability type affects the resolution time?
- Finding the attack types that have the highest average incident resolution time.
- Trends of each attack type per year.
- Identifying the most active attack source.
- Identifying the most targeted industries per country.
- Identifying the most active attack source per country.
- Key Insights from the Data
Most Common & Most Damaging Attack Types
-
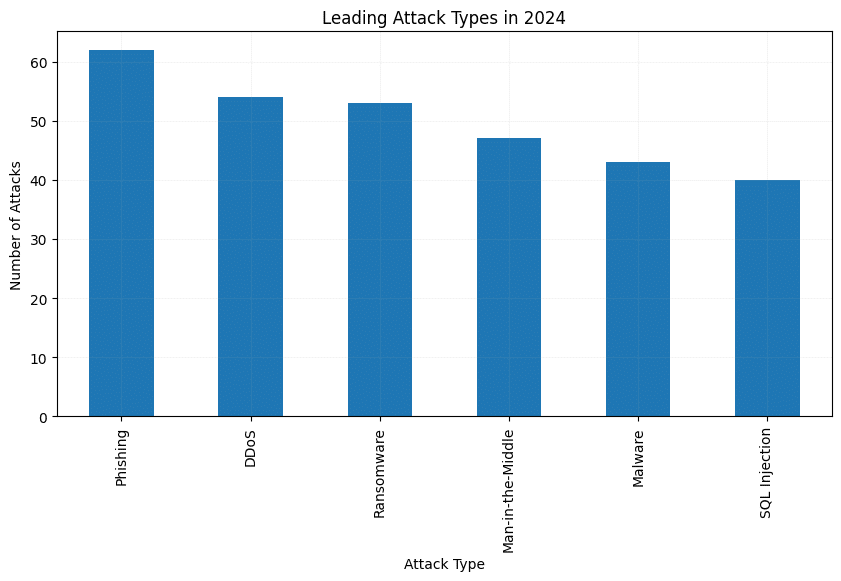
DDoS attacks are the most common, with 531 recorded incidents.
-
Man-in-the-middle attacks are the least common at 459 cases.
-
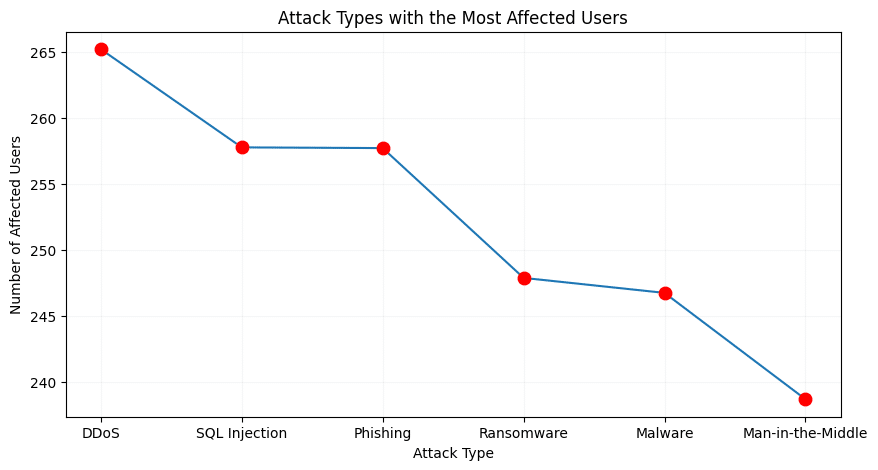
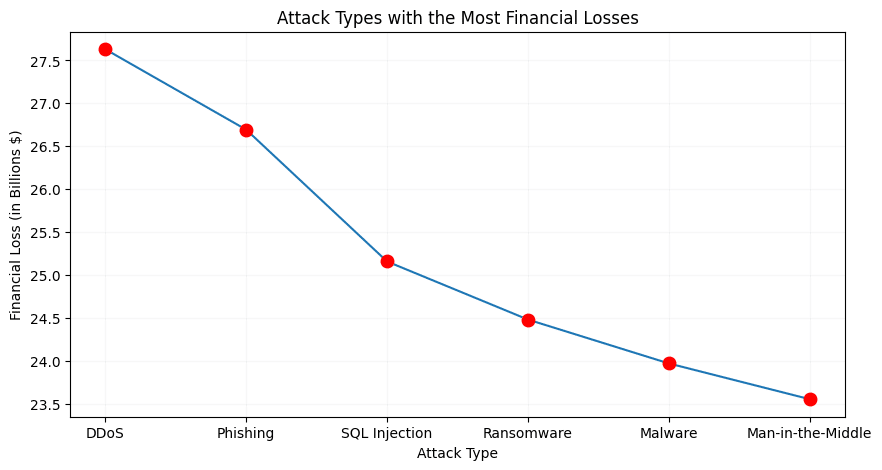
DDoS also leads in financial impact, causing $27.6 billion in losses and affecting 265 million users, more than any other attack type.
Most Targeted Industries
-
IT is the most attacked industry (478 attacks).
-
Government and telecommunications are the least targeted (403 each).
-
For example, DDoS attacks mainly target IT, telecom, and healthcare sectors.
Most Attacked Countries
-
The UK is the most affected country with 321 attacks.
-
China is the least affected, recording 281 incidents.
Most Common Vulnerabilities
-
Zero-day vulnerabilities are the leading cause of cyberattacks (785 attacks).
-
Weak passwords result in the fewest attacks (730), yet still significant.
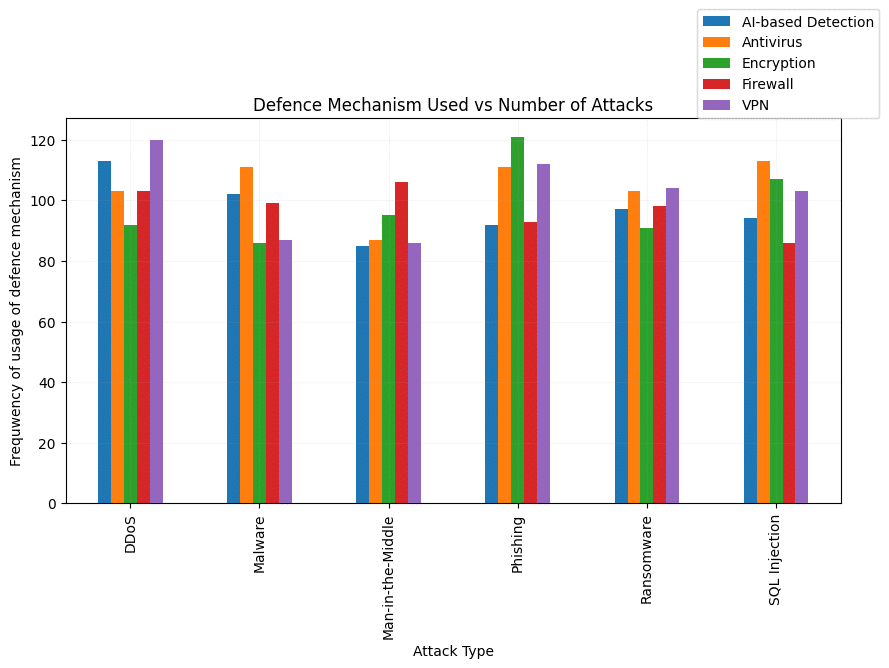
Most Used Defense Mechanisms
-
Antivirus software is the most commonly used defense.
-
AI-based detection is the least used, despite its growing importance.
Attack Trends Over the Years (2015–2024)
-
Phishing, malware, and DDoS dominate across the last decade.
-
Phishing spiked in 2016, 2020, and 2024, while malware led in 2015, 2022, and 2023.
Resolution Time by Attack and Vulnerability Type
-
Malware incidents take the longest to resolve (average 37.1 hours).
-
DDoS incidents are resolved fastest (35.6 hours).
-
Unpatched software leads to the longest resolution time (average 37.8 hours).
Financial Losses by Attack Type
-
Highest: DDoS ($27.6B)
-
Lowest: Man-in-the-middle ($23.5B)
Top Attack Sources Globally and Per Country
-
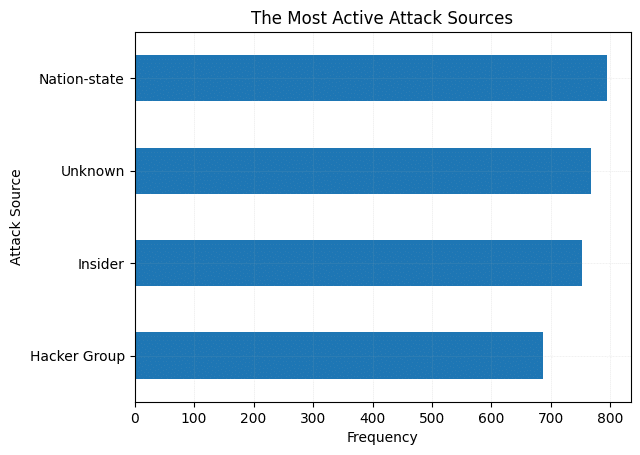
Nation-states are the most active attackers globally.
-
In countries like China, Russia, and Japan, nation-states and insiders are top sources.
-
Hacker groups are most active in the UK and Brazil.
Targeted Industries by Country
-
China: Education, IT, Healthcare
-
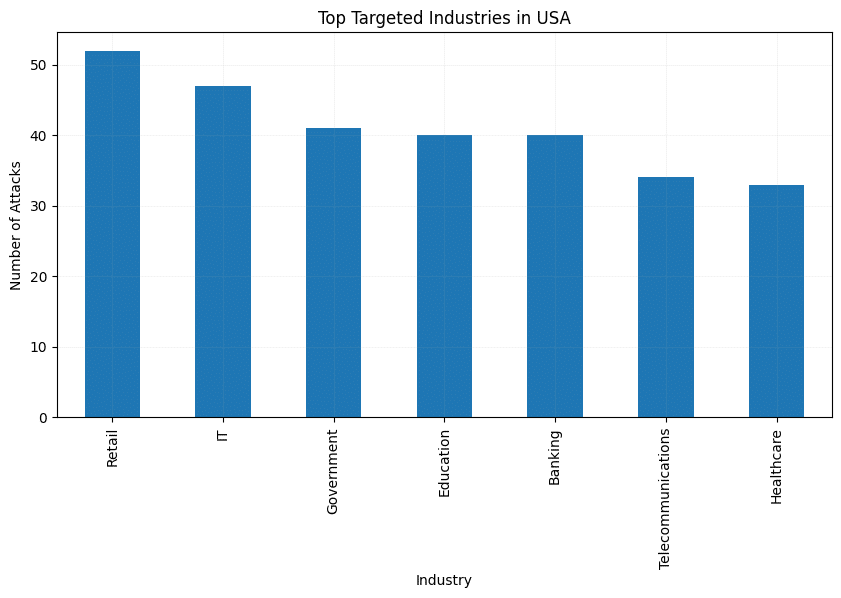
USA: Retail, IT, Government
-
Russia: Telecommunications, Banking, Education
-
India: IT, Banking, Government
- Data-Driven Recommendations
ased on patterns identified across attack types, industries, and countries, here are strategic recommendations to enhance your cybersecurity posture:
Best Practices for Cyber Defense
-
Install authentic antivirus software across all devices.
-
Avoid public Wi-Fi for sensitive transactions—use VPNs instead.
-
Stay away from non-HTTPS websites.
-
Use spam filters to block phishing attempts.
-
Always update your OS, applications, and firmware to patch vulnerabilities.
-
Set strong, unique passwords and enable multi-factor authentication (MFA).
-
Avoid saving sensitive credentials in password managers—especially for financial or classified systems.
-
Deploy and configure firewalls to segment your network and block malicious traffic.
This analysis reveals a sobering reality: cyberattacks are not only growing in volume but are also becoming more sophisticated and financially devastating. By understanding which attack types are on the rise, which sectors are under siege, and what defense mechanisms are most effective, organizations and governments can better prepare for the digital threats of today and tomorrow.
- Charts
- Want to Build Projects Like This?
Join our community and start learning Data Analytics, Machine Learning, and more, from zero to career-ready.
Leave a Reply Cancel reply
Need help? Our team is just a message away